Twitter/Access Issue | Elon Musk: Attack Originated from Ukrainian IPs

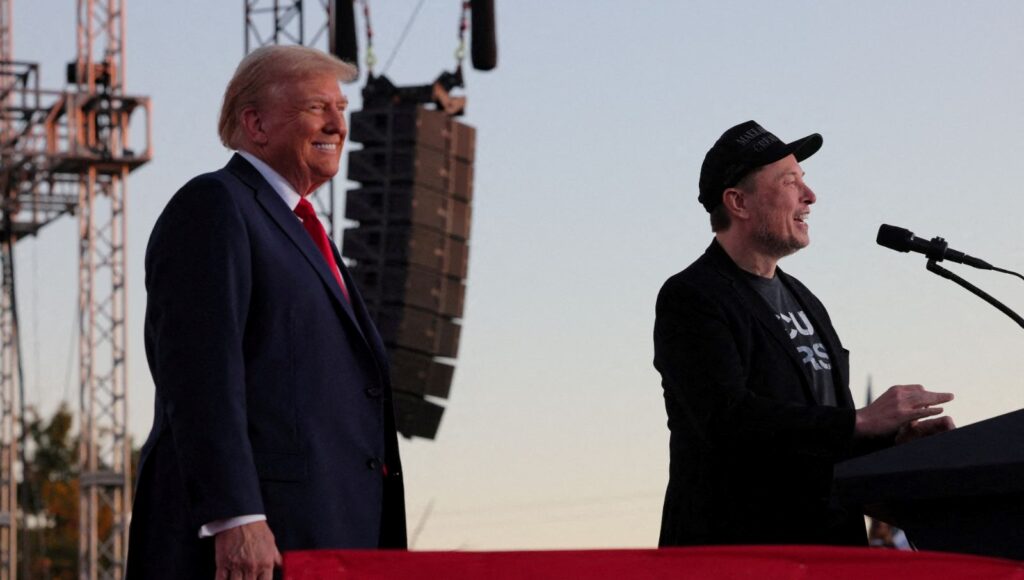
Owner of the social media platform X, Elon Musk, revealed that the access problem on the platform was caused by a “Ukrainian-origin cyber attack.” Musk stated, “We face attacks every day, but this one came from many sources.”
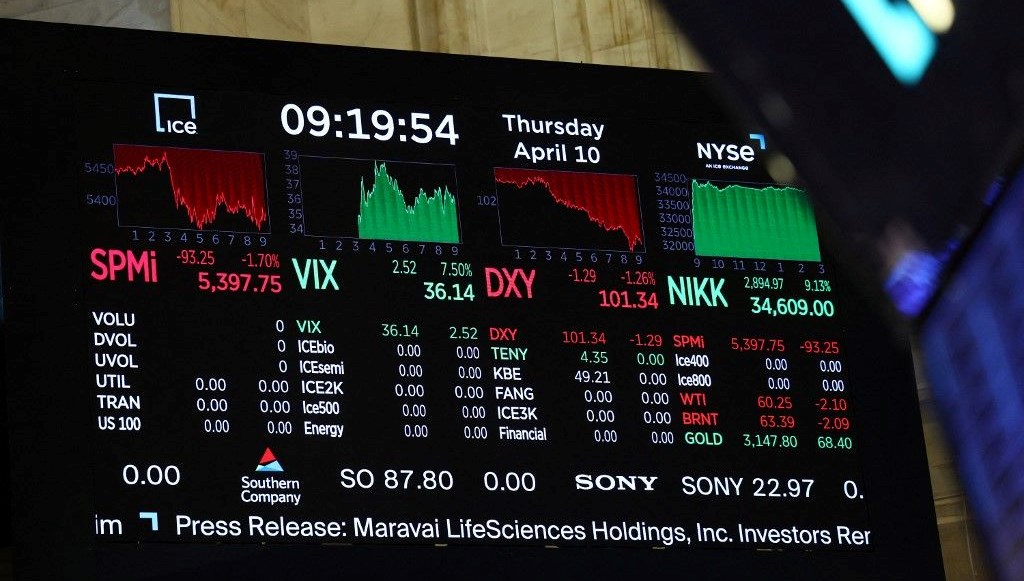
The social media platform X, owned by the American billionaire entrepreneur Elon Musk, experienced a prolonged access issue, with members unable to make posts for hours. According to Downdetector.com, which tracks when social media platforms go offline, the first outage on the X platform occurred around 6:30 am local time in New York. After a temporary fix for the problem, access-related issues on the platform increased around 9:40 am, with approximately 40,000 users reporting that X accounts were not working. It was noted that the outage occurred more in heavily populated cities on the east coast of the US, such as New York and Boston, and on the west coast in Los Angeles.
ELON MUSK: CYBER ATTACK ORIGINATED FROM UKRAINE
Elon Musk, the owner of X, stated that the problem on X since the morning was caused by a “cyber attack.” In an interview with Fox Business Network, Musk mentioned that they were not entirely sure about the nature of the attack but said, “However, a major cyber attack with Ukrainian IP addresses was launched to crash the X system.”
At the beginning of the attack, Musk had stated, “We face attacks every day, but this one came from many sources. It’s either a large, coordinated group or a country involved in this.” Musk confirmed that there are currently no access issues on the platform.
WHAT IS A CYBER ATTACK?
A cyber attack refers to attempts to infiltrate and cause damage to computer information systems, computer networks, infrastructures, personal computer devices, or smartphones in order to gain access to important documents and systems within a business or personal computer network. These attacks can be carried out for political, criminal, or personal purposes, aiming to destroy confidential information or gain access to it. Software that can bypass protection measures in computer network systems can cause harm to networks and systems.